In today’s world, technology dominates everything from the simplest to the most complex of activities. Software is undoubtedly the primary need of the market. Most organisations are trending towards cloud and multi-cloud implementations.
This move is not surprising since many are shifting to working remotely, and cloud computing has its share of benefits and challenges.
Describe SaaS.
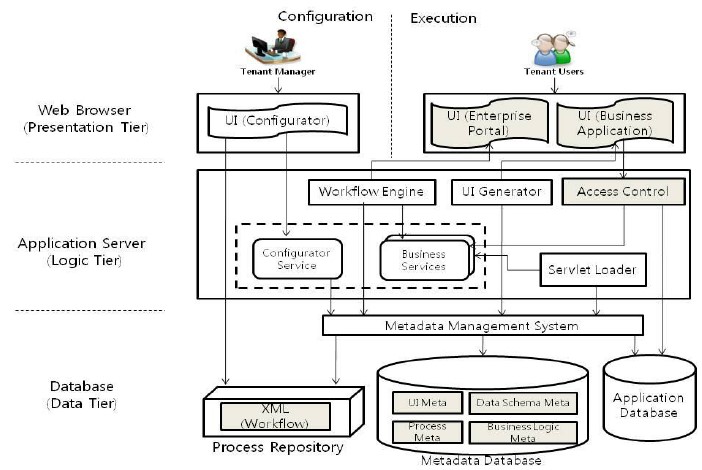
The on-demand, cloud-based software delivery service paradigm known as “Software as a Service” (SaaS) is common. Additionally, it is a cloud-based method of software and programme delivery. Users don’t install or operate the programme on their devices if you opt to subscribe to this model, so you may access apps without hosting them internally.
You may access the SaaS framework from anywhere as long as you have a device that can connect to the internet. Teams who operate remotely from all around the world would particularly benefit from this. As a result, the managers want to boost the output of their remote staff.
To give the workforce with the essential apps, organisations don’t need to construct and manage infrastructure. In a world that values technology, SaaS enables firms to expand more quickly.
advantages of SaaS
The worldwide SaaS industry has a promising future, and more people are utilising it. This positive development is brought on by:
1. Resources that can be scaled up or down on demand, depending on the needs of the organisation.
2. Only pay for what you use – Because companies only make purchases when necessary, they only pay for what they really use.
3. There is no waiting time, making adoption quick and simple. Instant access may be obtained by organisations, who can then assign workers. On-site apps, however, take longer to deploy.
4. Monthly or yearly membership fees are an affordable option for expanding enterprises because of how much less expensive they are.
5. Updates and maintenance are all taken care of by the SaaS provider, freeing up the company to concentrate on other important tasks.
6. You may use the SaaS platform via a web browser around-the-clock; there are no infrastructure or employee expenditures involved. There is no need to purchase any internal hardware or software licencing, and there is also no need to recruit people for on-site infrastructure and software maintenance.
Integration of
7. Application Programming Interfaces (APIs) is a simple process that SaaS may use to connect to other programmes.
8. Security – SaaS vendors make significant investments in security, such as by spreading servers among many regions and utilising automatic backups.
Recognising the necessity of SaaS security
Many SaaS providers host their customers’ accounts and offer SaaS services, security, and maintenance. Cloud-based SaaS security is often created to safeguard any software and data that the service carries. Organizations that store data in the cloud implement this set of recommended practises to safeguard their data. The platform, network, applications, operating system, and entire infrastructure must all be secured by the SaaS provider.
Although the supplier is solely accountable for SaaS security, both the consumer and the service provider are equally accountable. The National Cyber Security Center (NCSC) in the UK, for instance, mandates that both abide by SaaS security standards.
Because SaaS setups include a lot of sensitive data, cybercriminals frequently attack them. In the case of a security breach, data integrity and safety will be compromised. In the case of a security breach, data integrity and safety will be compromised. This might result in significant financial loss. You don’t require our reminders of the repercussions. Any hacker who is successful in getting into a SaaS system will cause absolute havoc.
Therefore, you may frequently experience service interruptions or security breaches if suppliers are not providing up to par services at all times. Therefore, carefully read the Service Level Agreement (SLA) before enrolling in any SaaS service, and ask any queries you may have to the supplier.
Businesses need to make sure they are following the finest procedures. Businesses will fail if this doesn’t happen, not to mention the numerous legal repercussions that will follow. Simply said, businesses that use the SaaS model must give SaaS security top priority. It requires making sure the right certifications are in place in addition to the practical component of environmental security.
Security issues with SaaS
SaaS poses a number of difficulties, including the following:
Complexity
As said, SaaS is a cloud-based service that serves numerous teams inside a business and occasionally across the world. Numerous consumers utilise SaaS programmes extensively across the board. All users are at various levels, having distinct positions, not to mention diverse levels of technical competence.
Even for specialised security teams, it makes SaaS products challenging to understand.
Communication
Whether it involves onsite or SaaS apps, this is a typical issue that arises in a business. The lack of team contact makes it difficult for the company to advance. Security vulnerabilities are sometimes brought about by communication breakdowns.
Collaboration
Teams frequently have unique objectives and duties. Unfortunately, the majority prioritise functionality and commercial needs before security. However, there is a constant need to strike a balance between commercial and security concerns. This is a major difficulty that needs routine team education.
fewer controls
Businesses that choose SaaS are dependent on outside providers to provide secure services. Even while service providers take every precaution to guarantee top-notch security and operation, service interruptions will occasionally occur. Businesses rely on the suppliers for constant uptime since they lack full control.
performing poorly
Performance problems are uncommon while using cloud services. A backup server will take over when one goes offline to keep the service running smoothly. However, if you’re far from a data centre, you can have some performance concerns. So, before enrolling, ask your provider where their data centres are located.
Best practises for SaaS
Moving your systems and procedures to SaaS is a smart step. However, you must first take into account both the current requirements of your company and the security requirements particular to SaaS.
You may assist the problem by maintaining the following cloud security best practises:
- Controlling and managing access
Your users need a way to log in in order to use the programme when you provide cloud-based apps to them. Applications that are appropriate for the cloud can only be accessed by those with the necessary permissions. To safeguard the user’s privacy and secure the communication route, you can utilise a Virtual Private Network (VPN).
Additionally, you may want to think about utilising additional security features like multi-factor authentication (MFA) or other stronger authentication techniques.
Any data requirements and workflow assignments must be taken into account by the system.
- Protection of Data
There are several recognised methods for users to connect with SaaS apps. All data must be protected from prying eyes by employing encryption and other security technologies on these channels. Data in transit can be encrypted and secured using the security protocol known as Transport Layer Security (TLS).
Additionally, to protect it from hackers, the data stored at rest in your servers and databases has to be encrypted. They can only be made available for use by guaranteeing data security through suitable security measures, especially for sensitive data. Surprisingly, SaaS-based security solutions are another option to explore for your cloud infrastructure.
Client- and server-side encryption, together with security management, should be offered by a SaaS provider. Particularly if any hardware is installed on-premises, detailed audit trails must be completed.
- Protection of Data
There are several recognised methods for users to connect with SaaS apps. All data must be protected from prying eyes by employing encryption and other security technologies on these channels. Data in transit can be encrypted and secured using the security protocol known as Transport Layer Security (TLS).
Additionally, to protect it from hackers, the data stored at rest in your servers and databases has to be encrypted. They can only be made available for use by guaranteeing data security through suitable security measures, especially for sensitive data. Surprisingly, SaaS-based security solutions are another option to explore for your cloud infrastructure.
Client- and server-side encryption, together with security management, should be offered by a SaaS provider. Particularly if any hardware is installed on-premises, detailed audit trails must be completed.
- Use antivirus and anti-malware software
Use cutting-edge antivirus and anti-malware software to guard against phishing and other assaults. These systems use real-time threat intelligence and behavioural analytics to detect and stop assaults and harmful files from propagating over cloud email and file-sharing services.
- Tools for CASB
The Cloud Access Security Broker, often known as CASB, is on-premises or cloud-hosted software that acts as a middleman between customers and SaaS providers. It’s employed to provide you the visibility you really need. You may use it to extend the security policies of your company’s on-site infrastructure to the cloud. You may also create brand-new regulations tailored to cloud computing.
CASB often acts as a hub for policy enforcement. It integrates several cloud security measures so that companies may utilise the service without risk. Spend some time investigating any security features that the SaaS provider may have, as you may employ CASB technologies to assist solve them.
High-risk user activity apps may be fixed and any security misconfigurations removed with the use of CASB tools. They can also monitor user access, identify any unlawful use of cloud services, and manage cloud services according to user, device, and application.
Consider the numerous CASB deployment options and pick the one that best suits your company.
Watching
Security in technology requires regular upgrades, just like any other technology. As a result, SaaS companies must upgrade the software and images for their standardised Virtual Machines (VM). All SaaS consumption must be kept track of and monitored. Information is likely to be useful in identifying any anomalies or unusual behaviour.
Analyze the information gathered by instruments like CASBs. Examine the logs that the SaaS provider has given. Be proactive, particularly with regard to security. Utilize systematic risk management combined with a mix of automated and human tools in the SaaS management systems. so that you can stay abreast of any modifications to SaaS usage, unusual conduct, or anything suspect.
These precautions are necessary to guarantee that SaaS users operate it safely and that you are in the know at all times.
- Network management
It is crucial to set security group control so that it may access particular network instances. Jump servers and Network Access Control Lists are examples of this (NACL).
For virtual private clouds, network-level control adds another degree of protection. To manage and monitor traffic to and from the subnets, this functions as a firewall.
This network layer control aids in the filtering of potentially harmful or suspicious traffic. This is done in accordance with a pre-configured set of guidelines for the acceptable traffic kinds on the network. Additionally, some organisations even deploy stronger security measures like preventive systems (IDS/IPS), which continue to monitor suspicious traffic long beyond the firewall.
- Appropriate oversight and incident response
For all sorts of occurrences, this entails establishing the relevant Standard Operating Procedures (SOPs). They must also record, make notes, report, and track activities till completion. Even for suspected security breaches, the investigative processes should be covered by the SOPs.
Scalability and dependability are
Because SaaS allows for both vertical and horizontal growth, it is popular. The former is constrained by the size of the server, whereas the latter concentrates on ways to link various pieces of hardware or software so they may still work together as a unified entity. A SaaS provider must have enough infrastructure redundancy to guarantee service continuity in order to account for this.
All SaaS suppliers ought to adhere to this best practise. Last but not least, a solid Disaster Recovery Plan (DRP) need to be in place to lessen any calamities.
Conclusion
Cloud computing will develop over time and pick up even more steam in the coming years. You may expect a more agile performance and more scalability using SaaS technologies at a lesser cost. Business will thus favour the SaaS framework.
SaaS can be a strong competitor, far better and more secure than on-site apps, especially for those in crucial financial and regulatory sectors, with the correct technology implemented and best practises in place. SaaS difficulties may be solved in order to support the long-term expansion of your company.





